Client errors
This page lists the error codes that can appear in the WARP client GUI. If you do not see your error below, refer to common issues or contact Cloudflare Support.
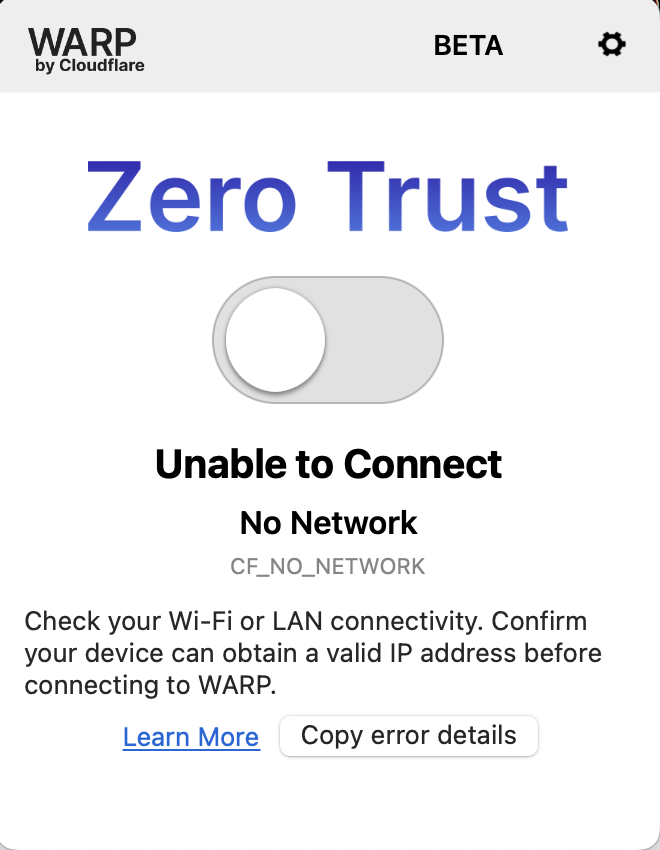
CF_CAPTIVE_PORTAL_TIMED_OUT
Symptoms
- Unable to login to a captive portal network
- No Internet connectivity
Cause
Captive portal detection is turned on and one of the following issues occurred:
- The user did not complete the captive portal login process within the time limit set by WARP.
- The captive portal redirected the user to a flow that is not yet supported by the captive portal detection feature.
Resolution
- Increase the captive portal timeout to allow users more time to login.
- If this does not resolve the issue, allow users to manually turn off WARP. We recommend setting an auto connect value so that the client turns itself back on after a few minutes.
CF_CONNECTIVITY_FAILURE_UNKNOWN
Symptoms
- Unable to connect WARP
- No Internet connectivity
- User may be behind a captive portal
Cause
The initial connectivity check failed for an unknown reason. Refer to Unable to connect WARP for the most common reasons why this error occurs.
Resolution
- Retrieve WARP debug logs for the device.
- Follow the troubleshooting steps in Unable to connect WARP.
CF_DNS_LOOKUP_FAILURE
Symptoms
- Unable to connect WARP
- Unable to browse the Internet
nslookupanddigcommands fail on the device
Cause
WARP was unable to resolve hostnames via its local DNS proxy.
Resolution
- Verify that the network the user is on has DNS connectivity.
- Verify that DNS resolution works when WARP is disabled.
- Ensure that no third-party tools are interfering with WARP for control of DNS.
- Ensure that no third-party tools are performing TLS decryption on traffic to the WARP IP addresses.
CF_DNS_PROXY_FAILURE
Symptoms
- Unable to connect WARP in a mode that enables DNS filtering.
Cause
A third-party process (usually a third-party DNS software) is bound to port 53, which is used by WARP’s local DNS proxy to perform DNS resolution. The name of third-party process will appear in the GUI error message.
On macOS, you may see mDNSResponder instead of the specific application name – mDNSResponder is a macOS system process that handles DNS requests on behalf of other processes. There is no known way to determine which process caused mDNSResponder to bind to port 53, but the most common culprits are virtual machine software (for example, Docker and VMware Workstation) and the macOS Internet Sharing feature.
Resolution
- Remove or disable DNS interception in the third-party process.
mDNSResponder
Below is a non-exhaustive list of third-party software that are known to cause mDNSResponder to bind to port 53. Rather than try to stop mDNSResponder, you should either configure the third-party software so that they no longer use port 53, or temporarily disable them before connecting to WARP.
- Docker: Turn off kernel networking for UDP in Docker.
- Internet Sharing feature: To disable Internet Sharing:
- On macOS, go to System Settings > General > Sharing.
- Turn off Internet Sharing.
- Certain VM software (such as VMware Workstation or Parallels): The presence of VM software does not guarantee that it is the offending program, since compatibility with WARP is highly dependent on the VM’s configuration. To work around the issue, connect to WARP before running any VMs:
- Stop/quit all VMs.
- Connect to WARP.
- Start the VMs again.
- Alternatively, switch WARP to Secure Web Gateway without DNS filtering mode.
CF_FAILED_READ_SYSTEM_DNS_CONFIG
Symptoms
- Unable to connect WARP
- Unable to browse the Internet
Cause
WARP could not read the system DNS configuration, most likely because it contains an invalid nameserver or search domain.
Resolution
On macOS and Linux, validate that /etc/resolv.conf is formatted correctly and check for invalid characters.
On Windows, validate that the registry entry HKLM\System\CurrentControlSet\Services\TCPIP\Parameters\SearchList contains only valid search domains. Examples of invalid entries include IP addresses and domains that start with a period (such as .local).
CF_FAILED_TO_SET_MTLS
Symptoms
- Unable to connect WARP
Cause
The device failed to present a valid mTLS certificate during device enrollment.
Resolution
- Ensure that there are no admin restrictions on certificate installation.
- Re-install the client certificate on the device.
CF_HAPPY_EYEBALLS_FAILURE
Symptoms
- Unable to connect WARP
Cause
A router, firewall, antivirus software, or other third-party security product is blocking UDP on the WARP ports.
Resolution
- Configure the third-party security product to allow the WARP ingress IPs and ports.
- Ensure that your Internet router is working properly and try rebooting the router.
CF_HOST_UNREACHABLE_CHECK
Symptoms
- Unable to connect WARP
- No Internet connectivity
- User may be behind a captive portal
Cause
The connectivity check inside of the WARP tunnel has failed.
Resolution
- Check for the presence of third-party HTTP filtering software (AV, DLP, or firewall) that could be intercepting traffic to the WARP IPs.
- In the third-party software, bypass inspection for all IP traffic going through WARP. To find out what traffic routes through the WARP tunnel, refer to Split Tunnels.
CF_INSUFFICIENT_DISK
Symptoms
- Unable to connect WARP
- OS warns that the disk is full
Cause
The hard drive is full or has incorrect permissions for WARP to write data.
Resolution
- Ensure that your device meets the HD space requirements for WARP.
- Check for disk permissions that may prevent WARP from using disk space.
- Empty trash or remove large files.
CF_INSUFFICIENT_FILE_DESCRIPTORS
Symptoms
- Unable to connect WARP
- Unable to open files on the device
Cause
The device does not have sufficient file descriptors to create network sockets or open files.
Resolution
Increase the file descriptor limit in your system settings.
CF_INSUFFICIENT_MEMORY
Symptoms
- Unable to connect WARP
- Device is very slow
Cause
The device does not have enough memory to run WARP.
Resolution
- Ensure that your device meets the minimum memory requirements for WARP.
- List all running processes to check memory usage.
CF_LOCAL_POLICY_FILE_FAILED_TO_PARSE
Symptoms
- Unable to connect WARP
Cause
The WARP client was deployed on the device using an invalid MDM configuration file.
Resolution
- Review the managed deployment guide for your operating system.
- Locate the MDM configuration file on your device.
- Ensure that the file is formatted correctly and only contains accepted arguments.
CF_NO_NETWORK
Symptoms
- Unable to connect WARP
- No Internet connectivity
Cause
The device is not connected to a Wi-Fi network or LAN that has connectivity to the Internet.
Resolution
- Launch the network settings panel on your device.
- Ensure that you are connected to a valid network.
- Check that your device is retrieving a valid IP address.
- If this does not resolve the error, try rebooting your device or running your system’s network diagnostics tool.
CF_REGISTRATION_MISSING
Symptoms
- Unable to connect WARP
Cause
The device is not authenticated to a Zero Trust organization because:
- The device was revoked in Zero Trust.
- The registration was corrupted or deleted for an unknown reason.
Resolution
- Launch the WARP client.
- Select the gear icon and go to Preferences > Account.
- Select Re-Authenticate Session.
- Complete the authentication steps required by your organization.
- If this does not resolve the error, select Logout from Cloudflare Zero Trust and then log back in. Logging out is only possible if Allow device to leave organization is enabled for your device.
CF_TLS_INTERCEPTION_BLOCKING_DOH
Symptoms
- DNS requests fail to resolve when WARP is turned on.
Cause
A third-party application or service is intercepting DNS over HTTPS traffic from WARP.
Resolution
Configure the third-party application to exempt the WARP DoH IPs.
CF_TLS_INTERCEPTION_CHECK
Symptoms
- Unable to connect WARP
Cause
A third-party security product on the device or network is performing TLS decryption on HTTPS traffic. For more information, refer to the Troubleshooting guide.
Resolution
In the third-party security product, disable HTTPS inspection and TLS decryption for the WARP IP addresses.