Microsoft Office 365 journaling setup with Cloud Email Security (formerly Area 1)
For customers using Microsoft Office 365, setting up Cloud Email Security via journaling is quick and easy. The following email flow shows how this works:
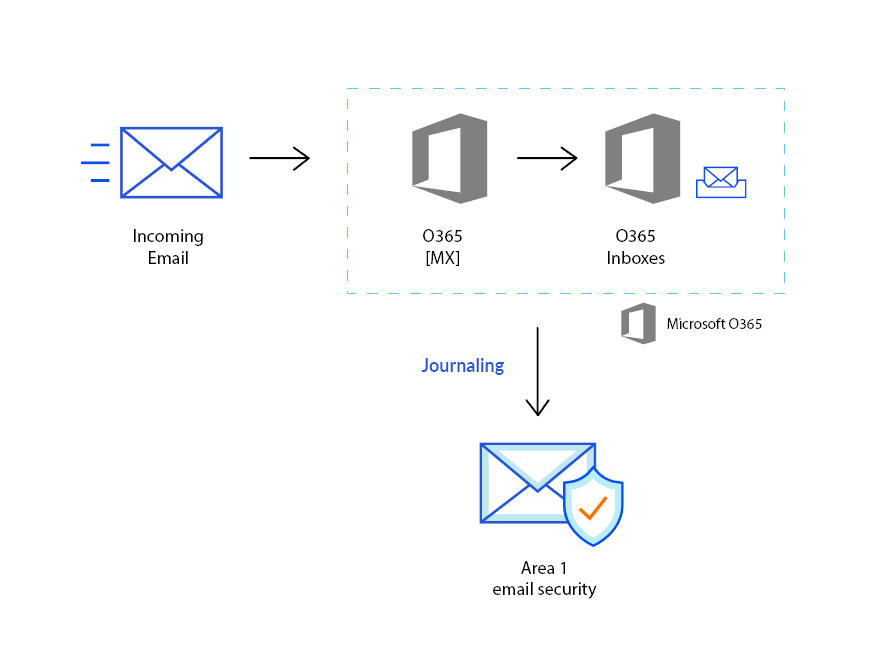
Journaling
1. Configure connector for delivery to Cloud Email Security (formerly Area 1) (if required)
If your email architecture does not include an outbound gateway, you can skip this step and proceed to the next one.
On the other hand, if your email architecture requires outbound messages to traverse your email gateway, you may want to consider configuring a connector to send the journal messages directly to Cloud Email Security.
Log in to the Exchange admin center, and go to Mail flow > Connectors.
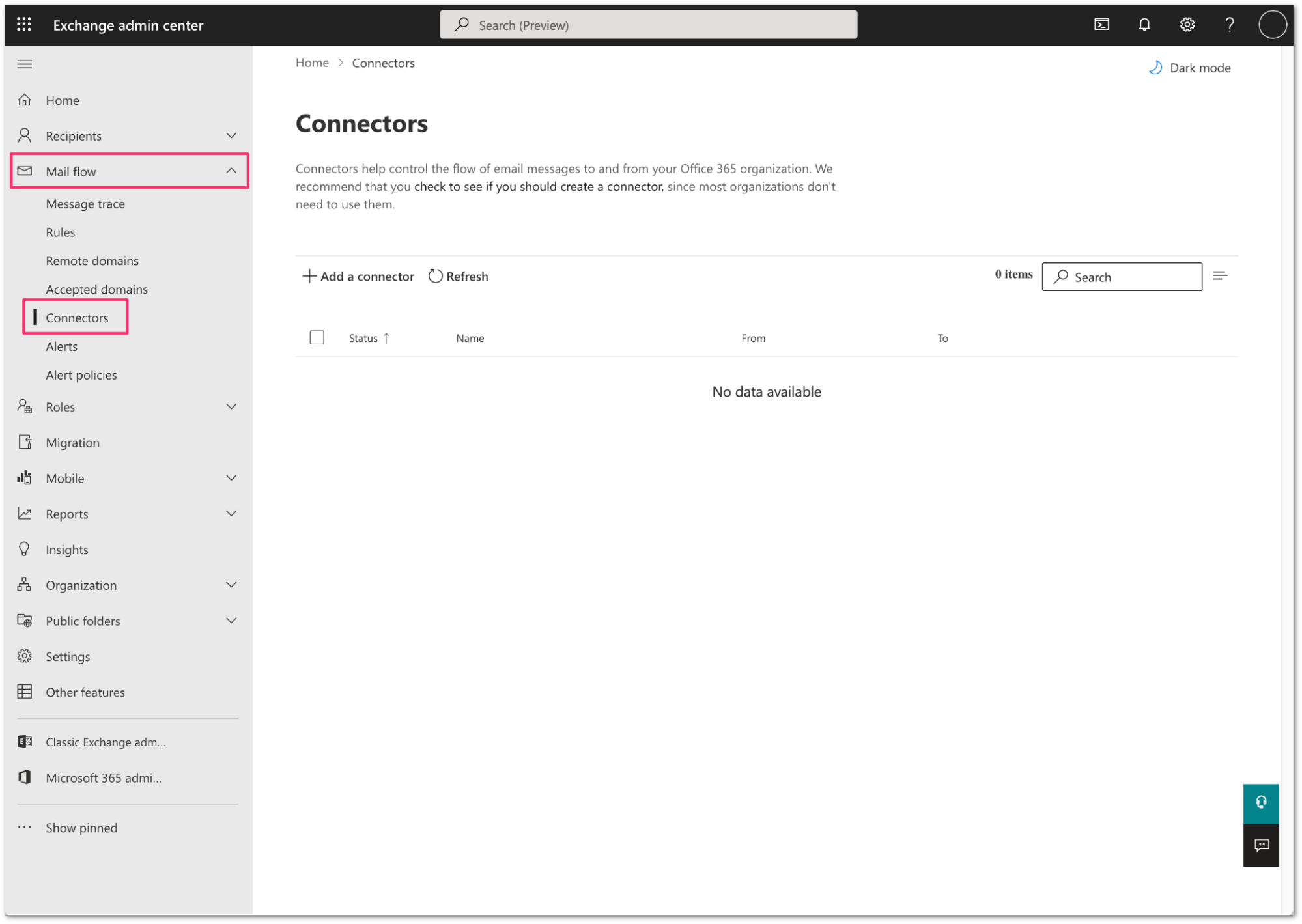
Select Add a connector.
Configure the new connector as follows:
- Connection From: Office 365
- Connection to: Partner Organization
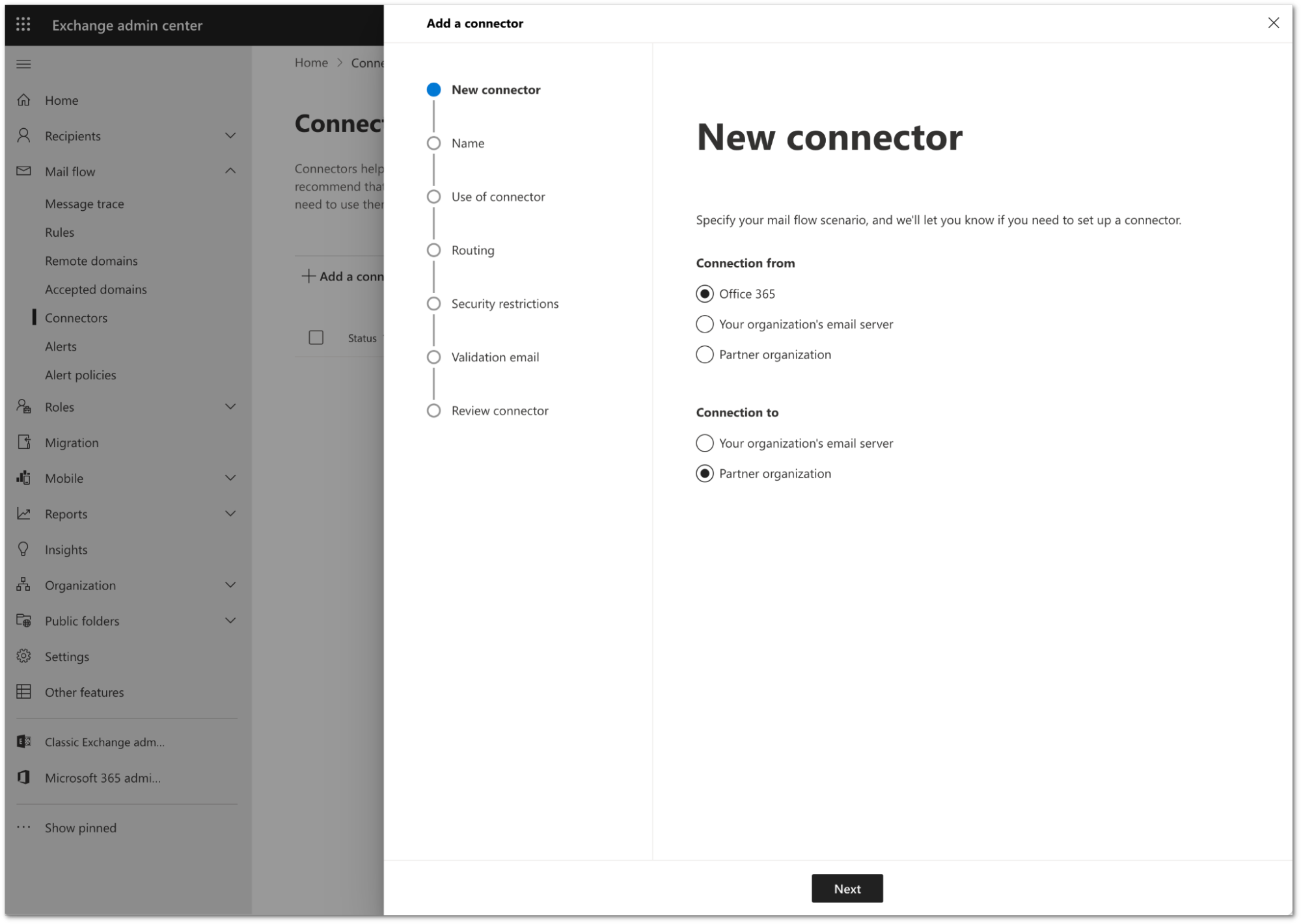
Select Next.
Configure the connector as follows:
- Name:
Deliver journal directly to Area 1 - Description:
Deliver journal directly to Area 1 - Turn it on: Enabled.
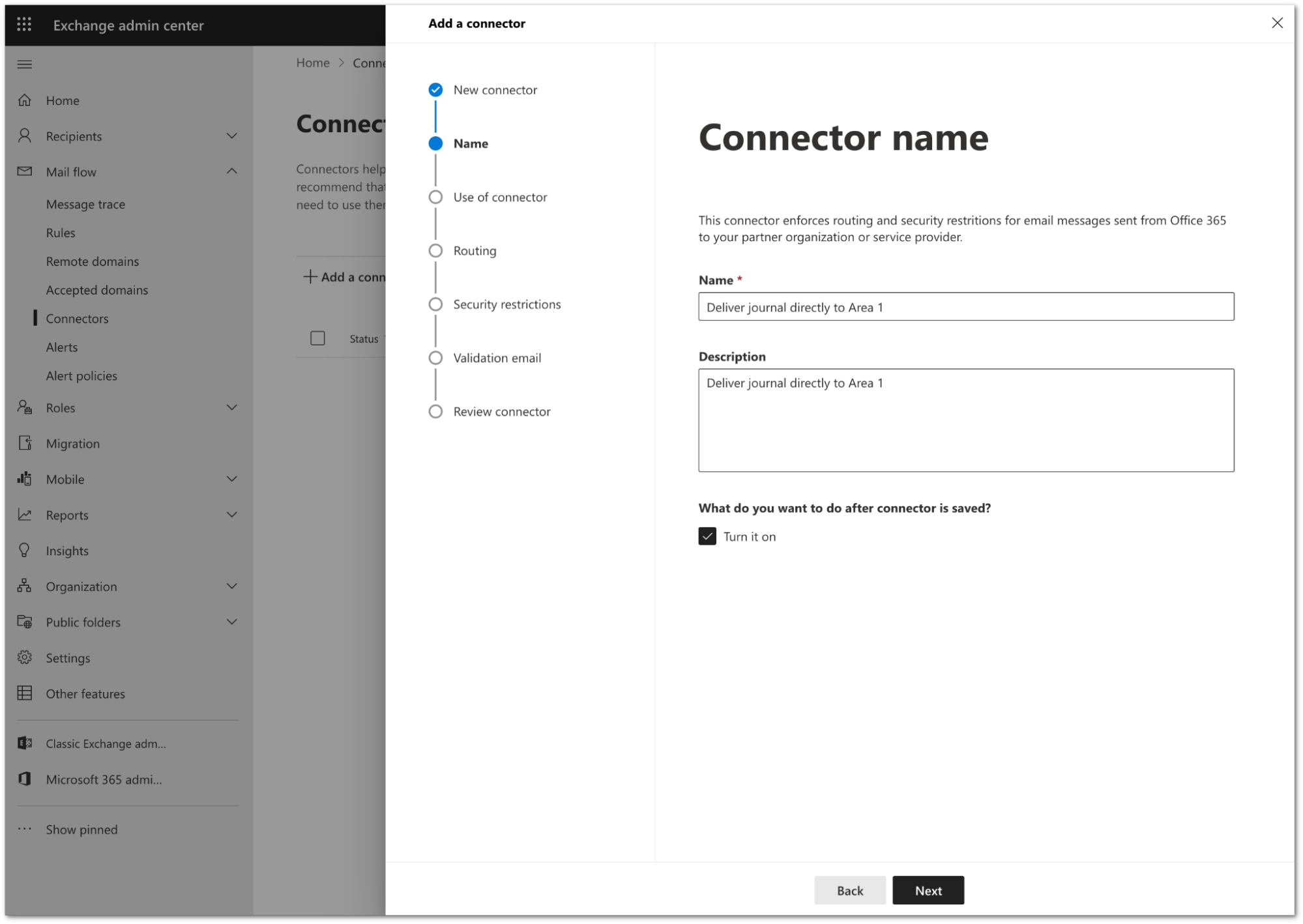
- Name:
Select Next.
Configure the Use of connector setting as follows:
- Select Only when email messages are sent to these domains.
- In the text field, enter
journaling.mxrecord.ioas the host address, and select + to add the domain.
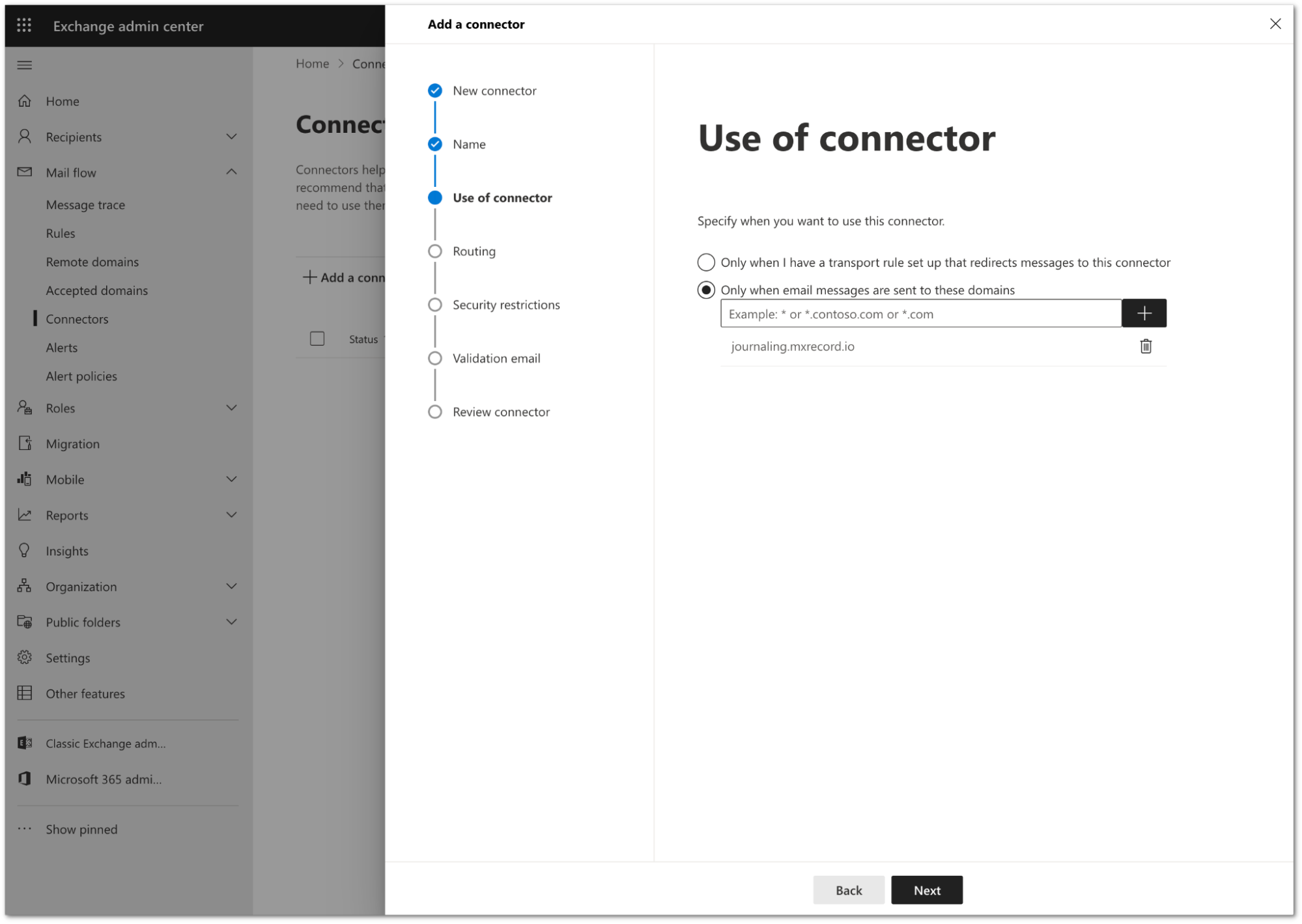
Select Next.
Configure the Routing setting as follows:
- Select Route email through these smart hosts.
- In the text field, enter
journaling.mxrecord.ioas the smart host address, and select + to add the domain.
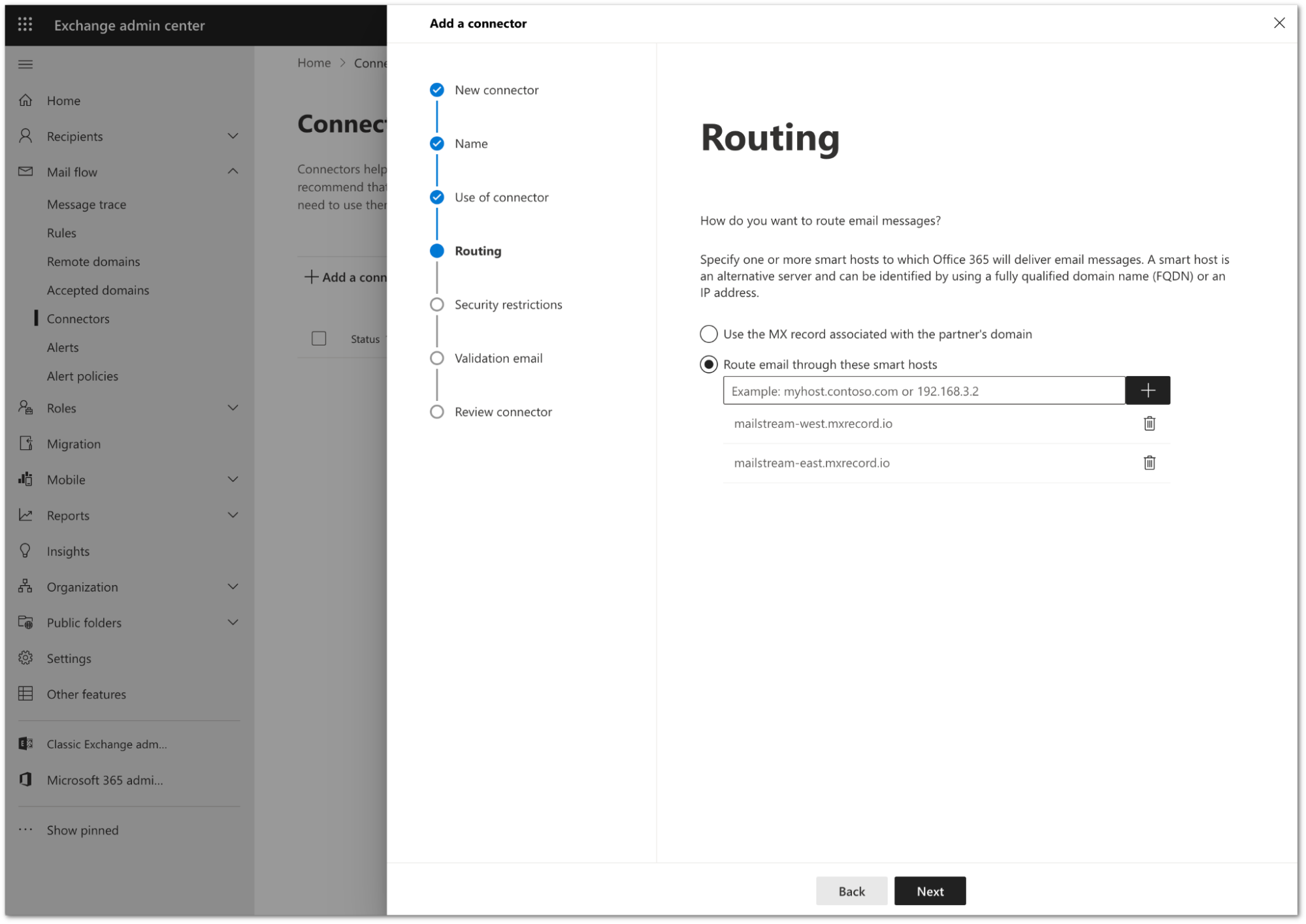
Select Next.
In Security restrictions, you need to keep the default TLS configuration. Review the following settings:
- Make sure the Always use Transport Layer Security (TLS) to secure the connection (recommended) checkbox is selected.
- In Connect only if the recipients email server certificate matches this criteria select Issued by a trusted certificate authority (CA).
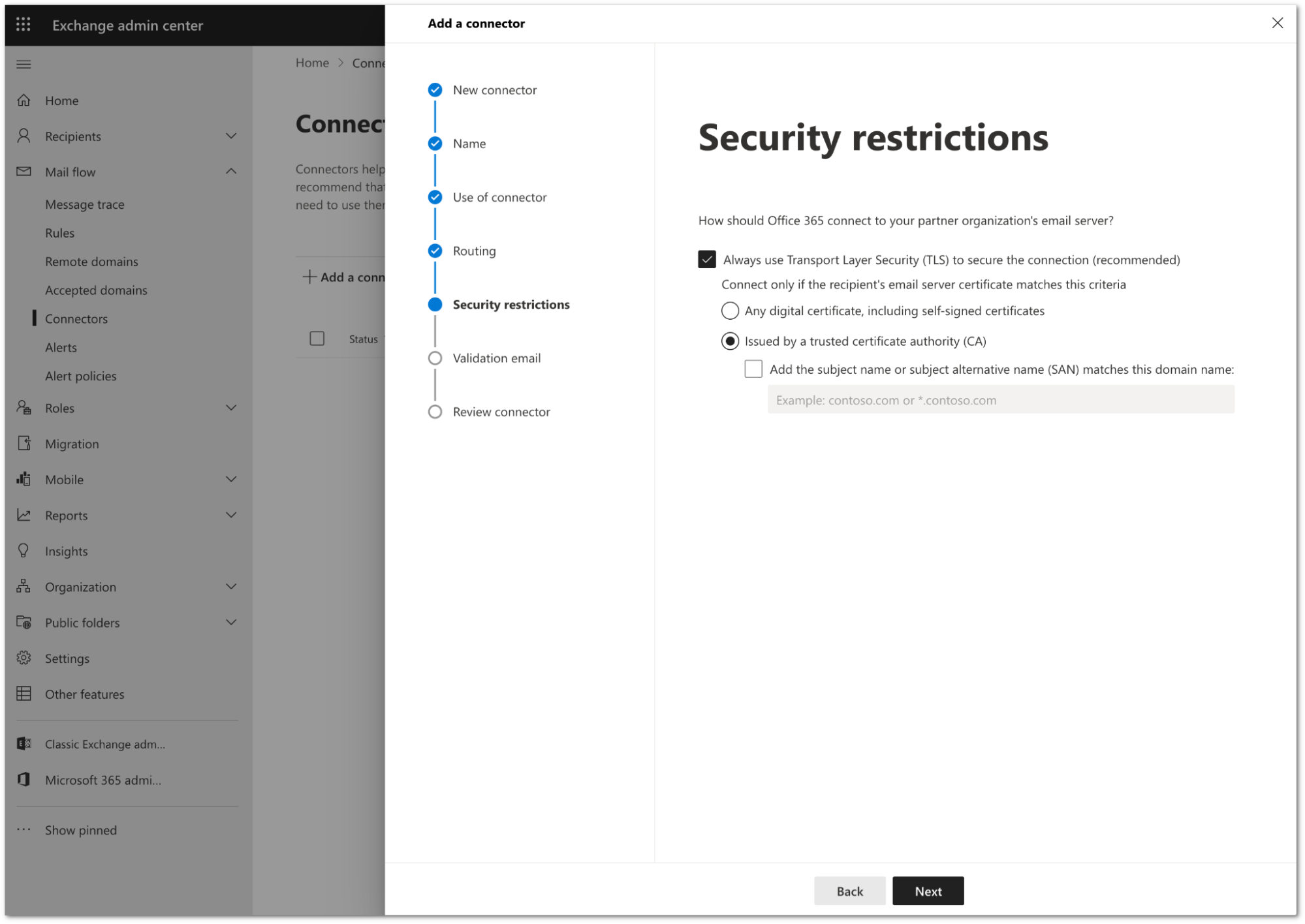
Select Next.
You need to validate the connector by using your tenant’s specific journaling address. To find this address, go to the Cloud Email Security dashboard > Support > Service Addresses page.
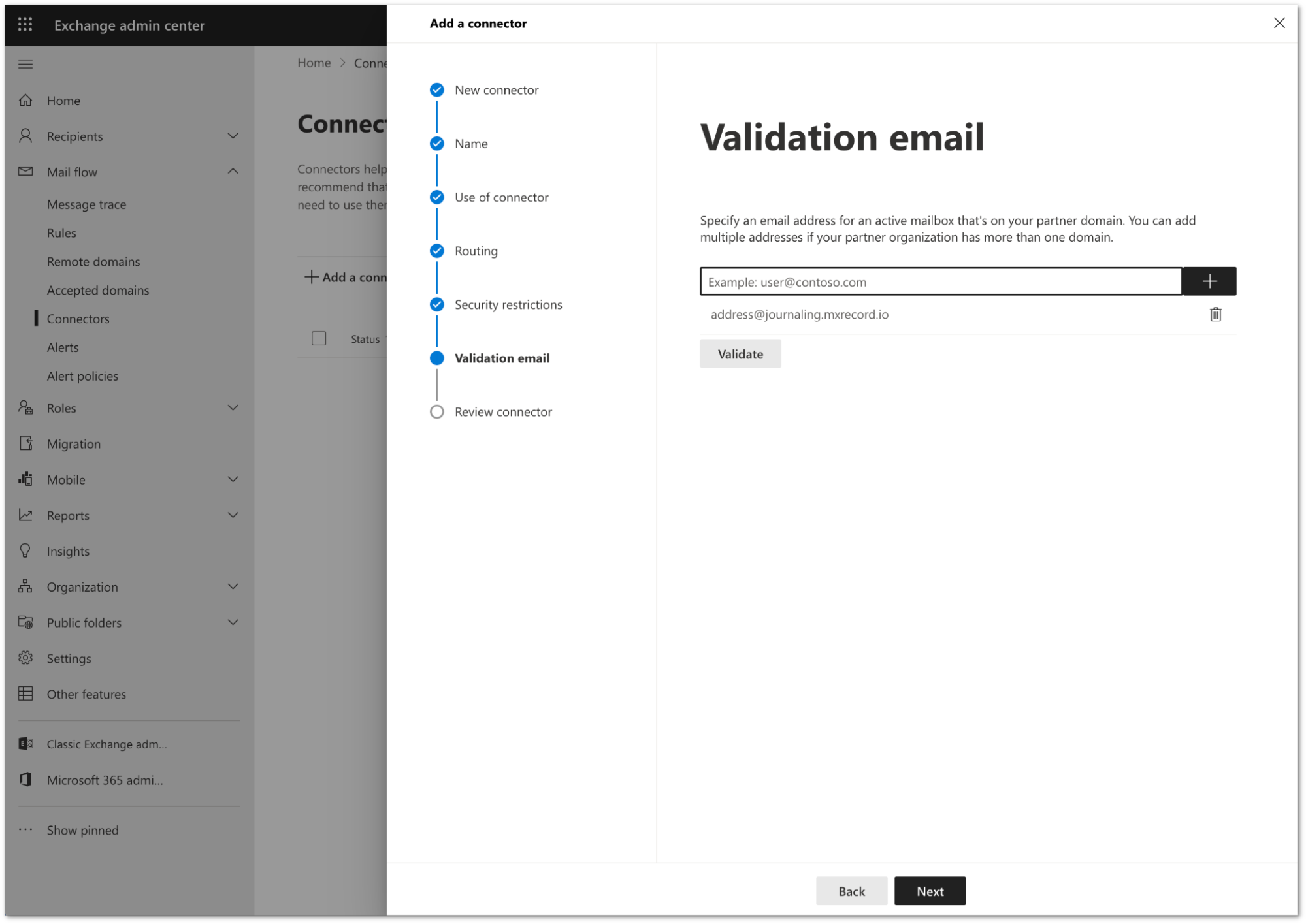
Add the address and select Validate.
Once the validation completes, you should receive a Succeed status for all the tasks. Select Next.
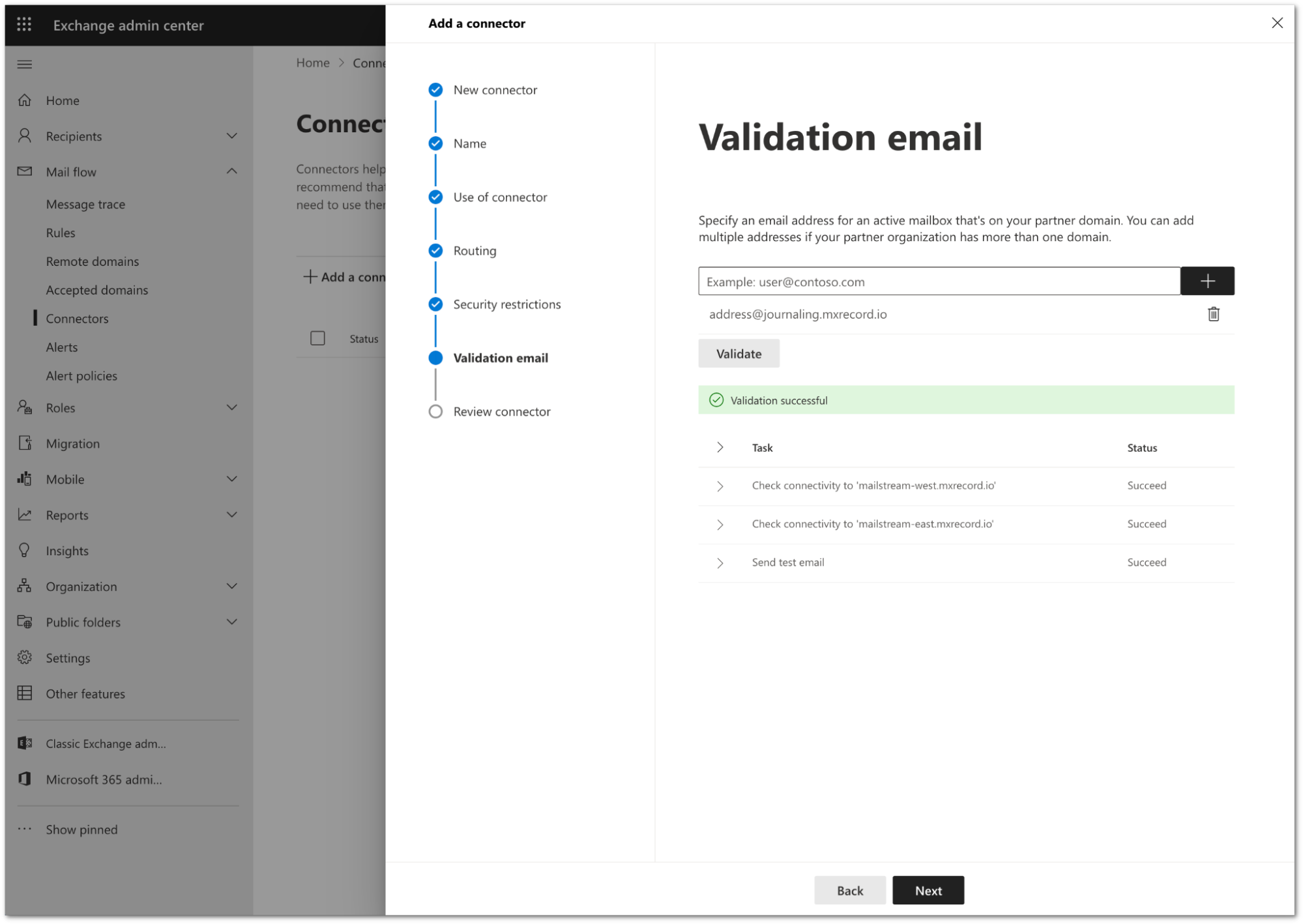
Review the configuration and select Create connector.
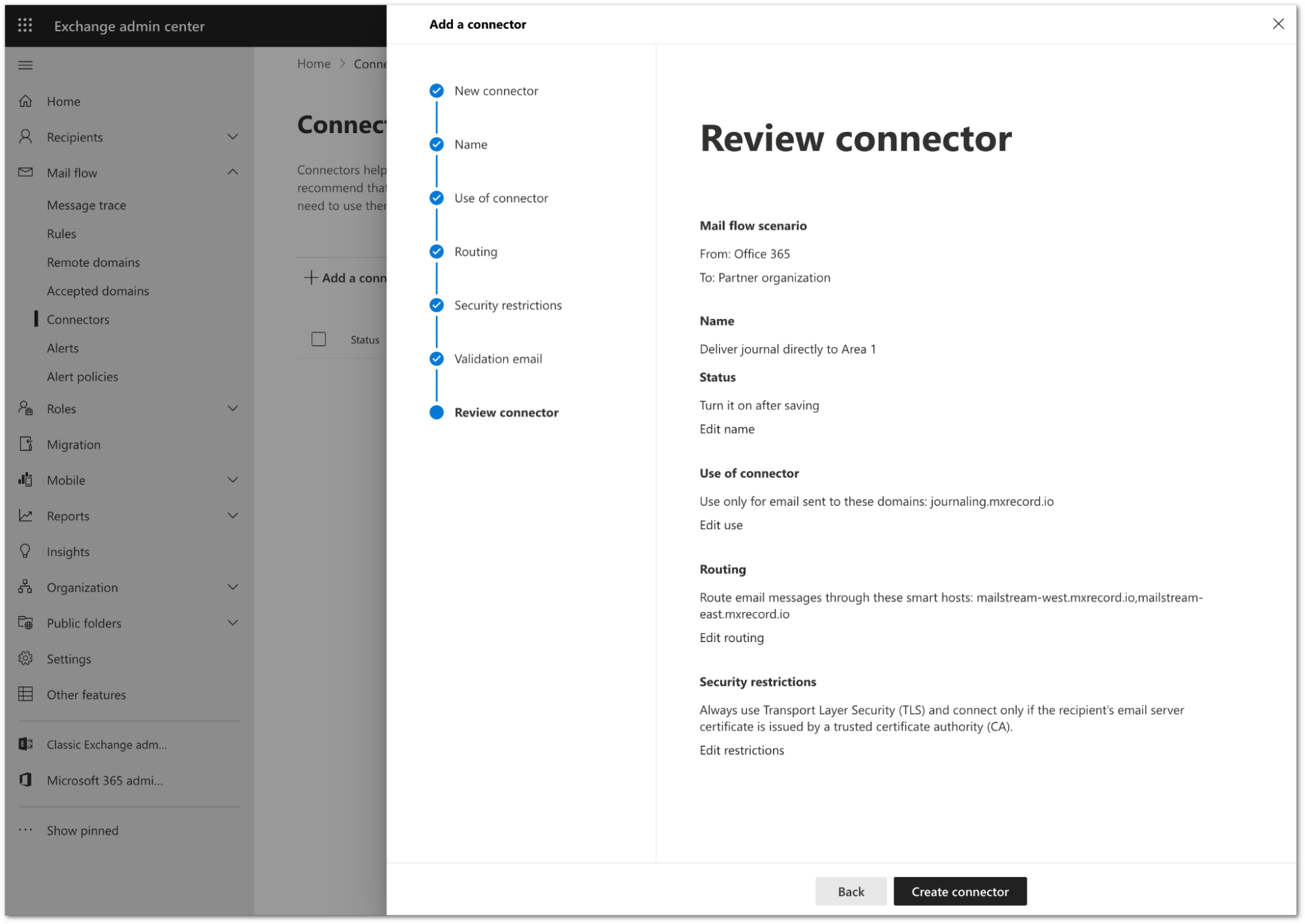
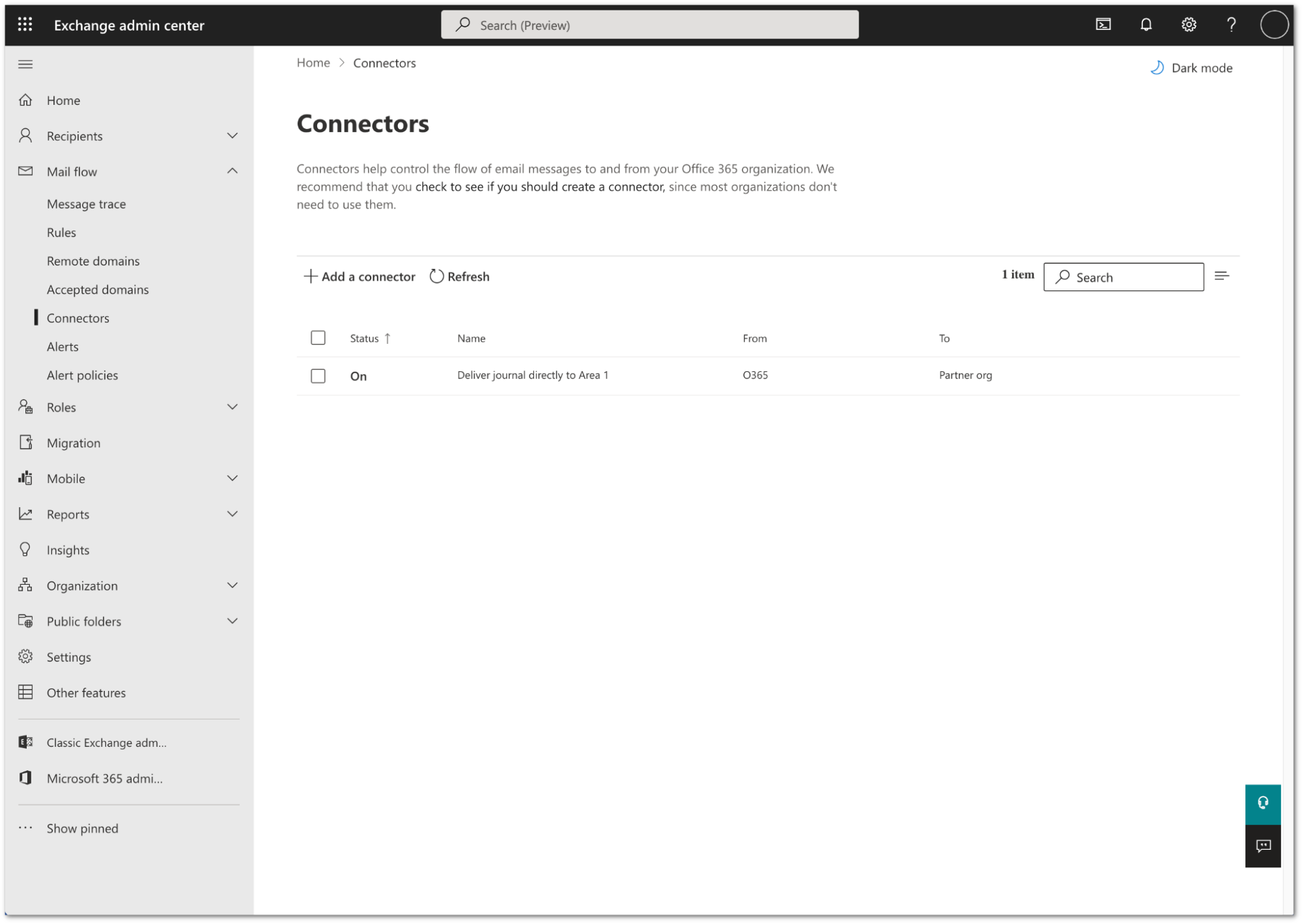
Your connector is now active. You can find it in Exchange admin center > Mail flow > Connectors.
2. Configure journal rule
Log in to the Microsoft Purview compliance portal.
Go to Data lifecycle management > Exchange (legacy).
Select Settings (the gear icon).
In Send undeliverable journal reports to enter the email address of a valid user account. Note that you cannot use a team or group address.
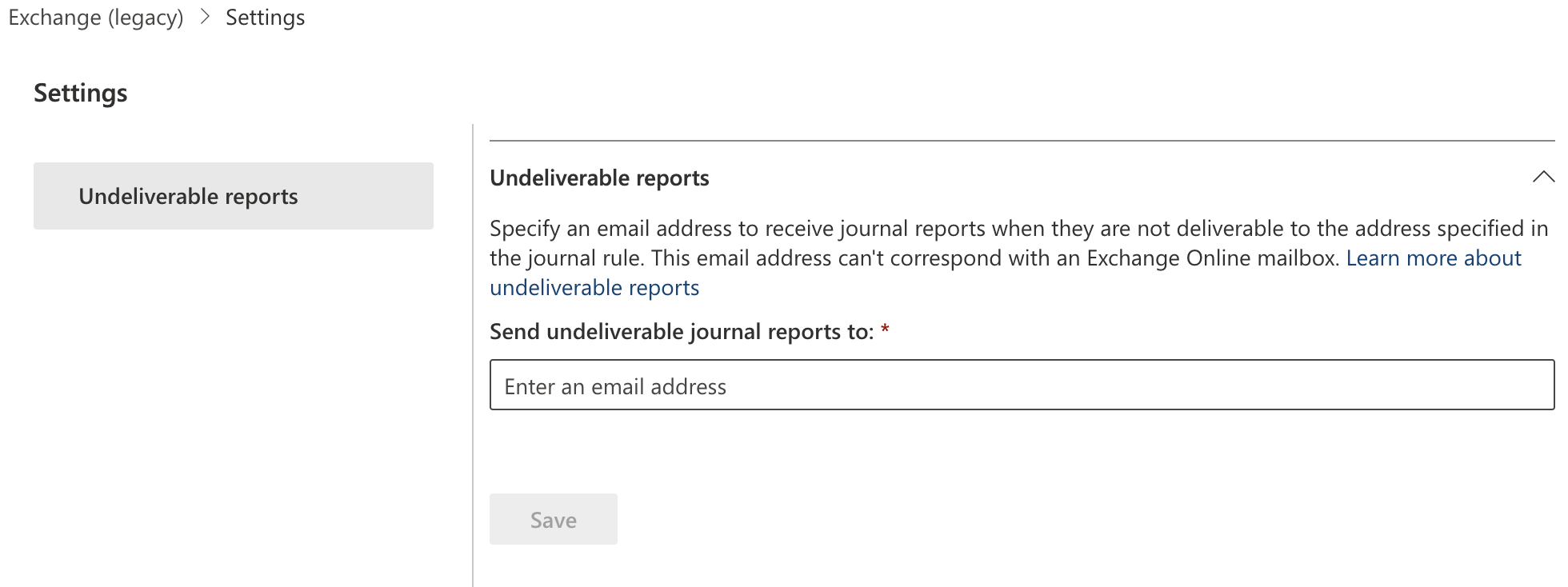
Select Save.
Still in the Exchange (legacy) screen, select Journal Rules.
Select New rule to configure a journaling rule, and configure it as follows:
- Send journal reports to: This address is specific to each customer tenant, and can be found in your Cloud Email Security dashboard. For example,
<customer_name>@journaling.mxrecord.io. - Journal Rule Name:
Journal Messages to CloudflareArea 1 - Journal messages sent or received from: Everyone
- Type of message to journal: External messages only
- Send journal reports to: This address is specific to each customer tenant, and can be found in your Cloud Email Security dashboard. For example,
Select Next.
Verify the information is correct, and select Submit > Done.
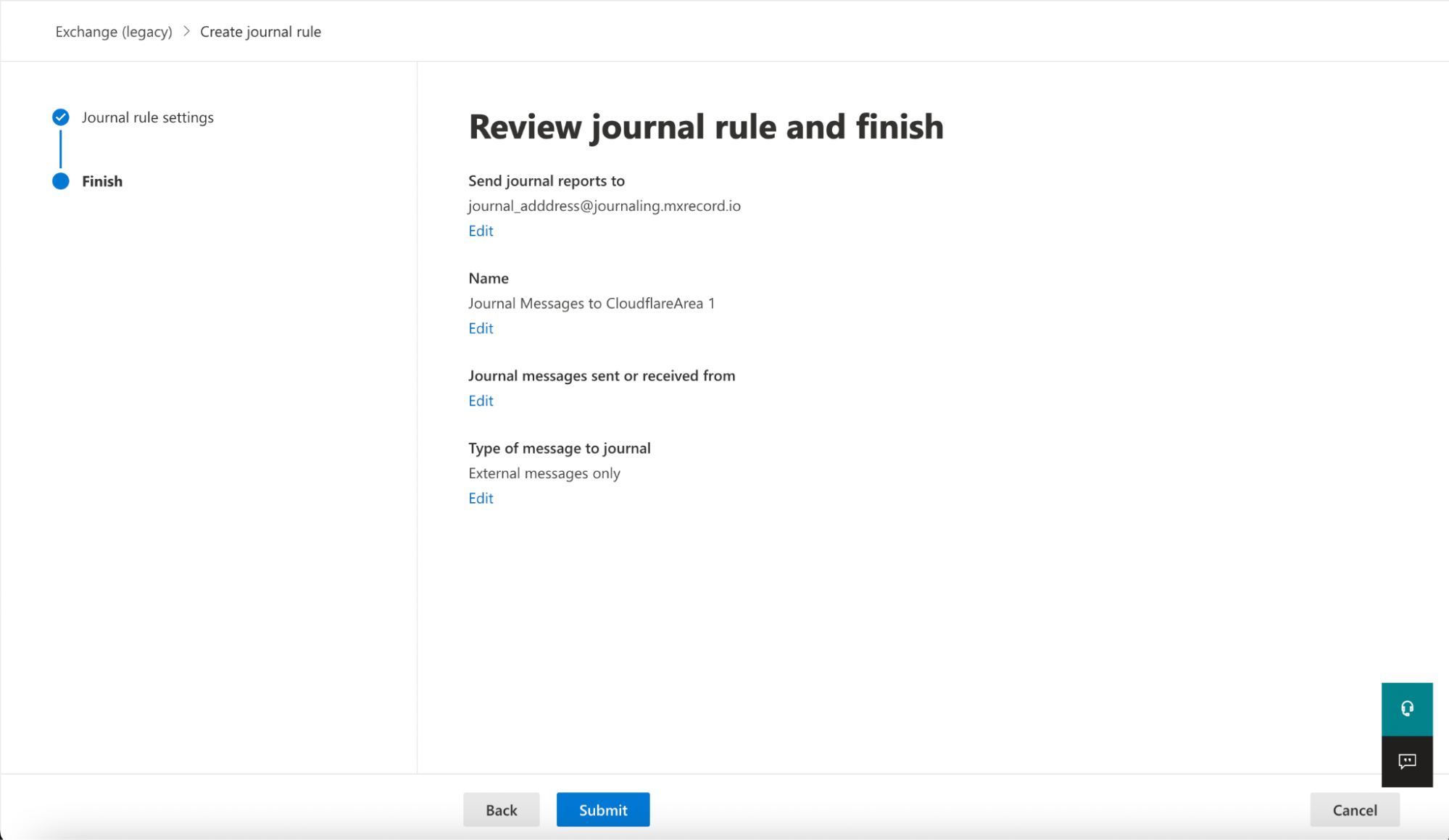
Once saved, the rule is automatically active. However, it may take a few minutes for the configuration to propagate and start pushing messages to Cloudflare Cloud Email Security. After it propagates, you can access the Cloudflare Cloud Email Security dashboard to check the number of messages processed. This number will grow as journaled messages are sent to Cloudflare Cloud Email Security from your Exchange server.
3. Compliance
Create Office 365 distribution lists
For compliance purposes, you might be required to process emails in certain geographic regions such as India or the EU. If that is your case, you should create Office 365 distribution lists for each geographic region where you need to process your emails, before configuring your journal rule.
Configure journal rule
After creating the distribution lists based on regions for your users, configure your journal rule:
Log in to the Microsoft Purview compliance portal.
Go to Data lifecycle management > Exchange (legacy).
Select Settings (the gear icon).
In Send undeliverable journal reports to enter the email address of a valid user account. Note that you cannot use a team or group address.

Select Save.
Still in the Exchange (legacy) screen, select Journal Rules.

Select New rule to configure a journaling rule, and configure it as follows:
- Send journal reports to: This address is specific to each customer tenant, and can be found in your Cloud Email Security dashboard. If you need to process emails in certain geographic regions, refer to the Geographic locations table for more information on what address you should use.
- Journal Rule Name:
Journal Messages to CloudflareArea 1 - Journal messages sent or received from: A specific user or group and select the user group you created above.
- Type of message to journal: External messages only
Select Next.
Verify the information is correct, and select Submit > Done.

Once saved, the rule is automatically active. However, it may take a few minutes for the configuration to propagate and start pushing messages to Cloudflare Cloud Email Security. After it propagates, you can access the Cloudflare Cloud Email Security dashboard to check the number of messages processed. This number will grow as journaled messages are sent to Cloudflare Cloud Email Security from your Exchange server.
Geographic locations
Select from the following BCC addresses to process email in the correct geographic location.
Host| Location | Note | <customer_name>@journaling.mxrecord.ioUS | Best option to ensure all email traffic processing happens US data centers. | <customer_name>@journaling.mailstream-eu-primary.mxrecord.ioEU | Best option to ensure all email traffic processing happens in Germany, with fallback to US data centers. | <customer_name>@journaling.mailstream-eu1.mxrecord.ioEU | Best option to ensure all email traffic processing happens within the EU without fallback to US data centers. | <customer_name>@journaling.mailstream-bom.mxrecord.mxIndia | Best option to ensure all email traffic processing happens within India. | <customer_name>@journaling.mailstream-india-primary.mxrecord.mxIndia | Same as | mailstream-bom.mxrecord.mx, with fallback to US data centers.<customer_name>@journaling.mailstream-asia.mxrecord.mxIndia | Best option for companies with a broader Asia presence. | <customer_name>@journaling.mailstream-syd.area1.cloudflare.netAustralia / New Zealand | Best option to ensure all email traffic processing happens within Australia. | <customer_name>@journaling.mailstream-australia.area1.cloudflare.netAustralia / New Zealand | Best option to ensure all email traffic processing happens in Australia, with India and US data centers as backup. | |
|---|