Security Analytics
Security Analytics displays information about all incoming HTTP requests for your domain, including requests not handled by Cloudflare security products.
Use the Security Analytics dashboard to:
- View the traffic distribution for your domain.
- Understand which traffic is being mitigated by Cloudflare security products, and where non-mitigated traffic is being served from (Cloudflare global network or origin server).
- Analyze suspicious traffic and create tailored WAF custom rules based on applied filters.
- Learn more about Cloudflare’s security scores (attack score, bot score, uploaded content scanning results) with real data.
- Find an appropriate rate limit for incoming traffic.
If you need to modify existing security-related rules you already configured, consider also using the Security Events dashboard. This dashboard displays information about requests affected by Cloudflare security products.
Access
To use Security Analytics:
Log in to the Cloudflare dashboard and select your account.
Go to the account or zone dashboard:
- For the zone dashboard, select your domain and go to Security > Analytics.
- For the account dashboard, go to Security Center > Security Analytics.
Adjusting displayed data
Apply filters
Adjust the scope of analytics by manually entering filter conditions. You can also select Filter or Exclude to filter by a field value. These buttons appear when you hover the analytics data legend.
To manually add a filter:
- Select Add filter.
- Select a field, an operator, and a value. For example, to filter events by source IP address, select the Source IP field, select the equals operator, and enter the IP address.
- Select Apply.
Take the following into account when entering filter values:
- Do not add quotes around values.
- Do not enter the
ASprefix when entering ASN numbers. For example, enter1423instead ofAS1423. - Wildcards are not supported.
Select time frame
Select the time frame you wish to analyze from the Previous 24 hours drop-down list.
Create custom rule from current filters
To create a custom rule with an expression based on the filters you applied in Security Analytics, select Create custom rule above the main chart.
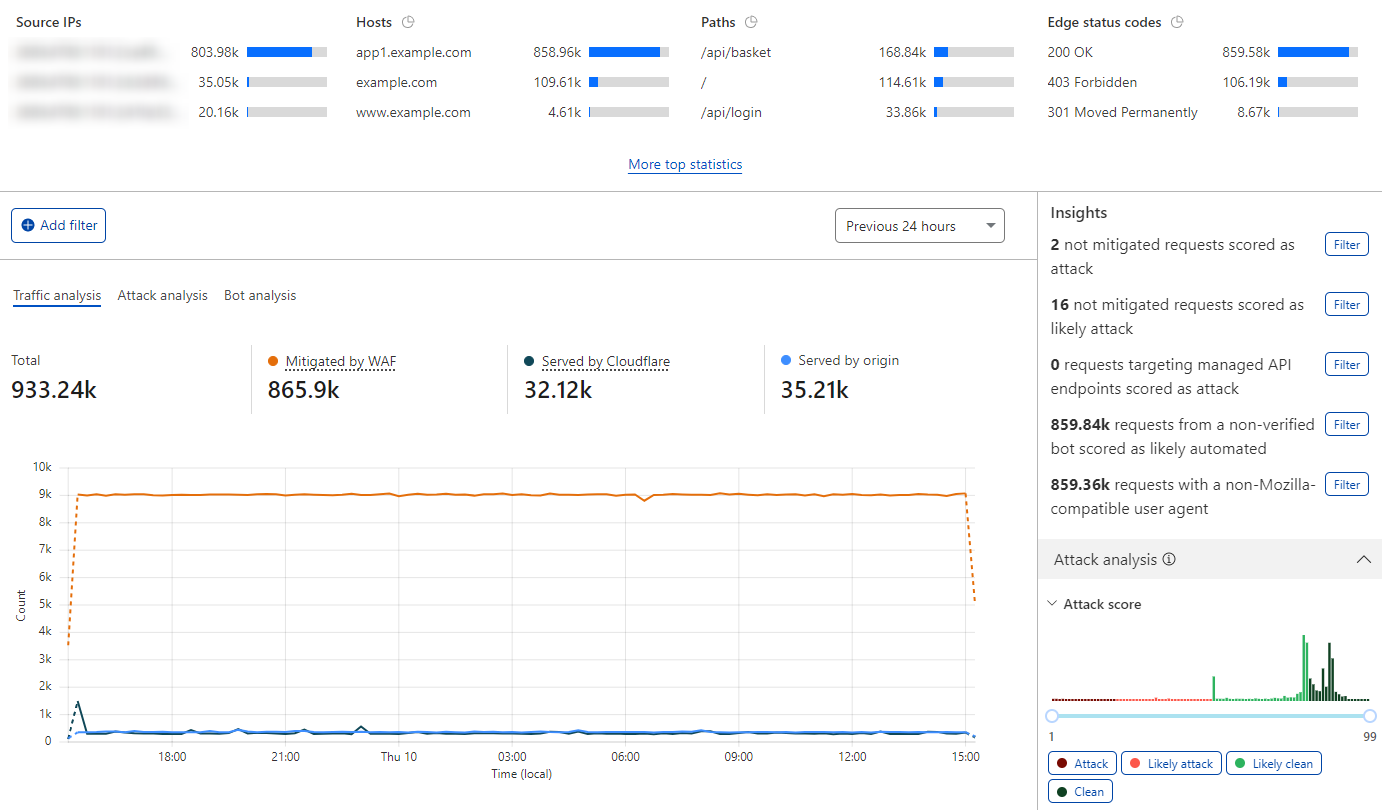
Main dashboard areas
Top statistics
This section presents top statistics about incoming requests highlighting relevant properties commonly used when performing a security analysis.
You can filter or exclude some of the top values by selecting Filter or Exclude next to each value.
To display additional top statistics, select More top statistics.
Insights
The provided insights show statistics for commonly used filters when doing security analyses, without immediately applying these filters to the displayed data.
If you find a high value in one or more insights, this can mean that there is a set of suspicious requests that you should investigate. Additionally, these insights are a good starting point for applying a first set of filters to the dashboard.
To apply the filters for an insight to the data displayed in the Security Analytics dashboard, select Filter next to the insight.
Score-based analyses
The Attack likelihood, Bot likelihood, and Malicious uploads sections display statistics related to WAF attack scores, bot scores, and WAF content scanning scores of incoming requests for the selected time frame.
You can examine different traffic segments according to the current metric (attack, bot, or content scanning). To apply score filters for different segments, select the buttons below the traffic chart. For example, select Likely attack under Attack likelihood to filter requests that are likely an attack (requests with WAF attack score values between 21 and 50).
Additionally, you can use the slider tool below the chart to filter incoming requests according to the current metric. This allows you to filter traffic groups outside the predefined segments.
Main chart
The main chart displays the following data for the selected time frame, according to the selected tab:
Traffic analysis: Traffic mitigated by the Cloudflare security platform, served by Cloudflare, and served by the origin server, according to the following classification:
- Mitigated by WAF: Requests blocked or challenged by Cloudflare’s application security products such as the WAF and HTTP DDoS protection. It does not include requests that had the following actions applied: Log, Skip, and Allow.
- Served by Cloudflare: Requests served by the Cloudflare global network such as cached content and redirects.
- Served by origin: Requests served by your origin server.
Attack likelihood: WAF attack score analysis of incoming requests, classifying them as Clean, Likely clean, Likely attack, or Attack.
Bot likelihood: Bot score analysis of incoming requests, classifying them as Automated, Likely automated, or Likely human.
Rate limit analysis: Displays data on the request rate for traffic matching the selected filters and time period. Use this tab to find an appropriate rate limit for incoming traffic matching the applied filters.
AI Assistant Beta: Get insights about your application security by using plain language to interrogate your data. For more information, refer to our blog post.
Logs
Security Analytics shows request logs for the selected time frame and applied filters, along with detailed information and security analyses of those requests.
By default, Security Analytics uses sampled logs for the logs table. If you are subscribed to Log Explorer Beta, you may also have access to raw logs.
Sampled logs
This section contains detailed log information for individual (sampled) requests in the selected time frame.
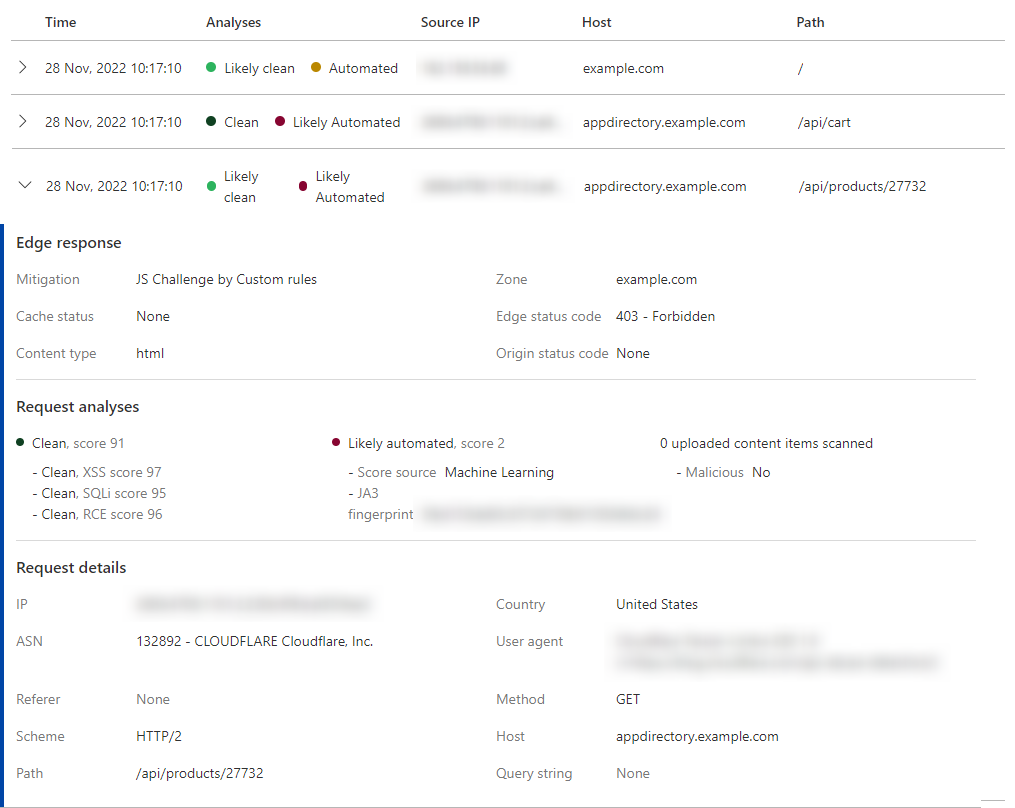
The displayed information includes:
- Mitigation action applied to the request
- Cache status
- Status code returned by the origin server to Cloudflare (in case of a cache miss)
- Status code returned by Cloudflare to the client
- Security scores for the request (attack, bot, uploaded content scanning)
- Request properties
Raw logs
When performing a forensic analysis, you sometimes select a very short time frame and apply several filters to identify a specific set of requests. In this situation, to get a better understanding of the incoming requests at a given point in time, you would require the full list of requests and not just a sample.
By default, Security Analytics shows sampled logs based on the filters you apply. Under certain conditions, you can switch to Raw logs. This view shows all the request logs for the selected time frame and filters instead of sampled logs. At this time, this view is only available when the number of sampled logs shown in the Security Analytics page is lower than 100.
View raw logs
To switch from sampled logs to raw logs, select Switch to raw logs under Sampled logs. This option is only available when the number of (sampled) logs for the selected time frame is lower than 100.
To switch from raw logs back to sampled logs, select Switch back to sampled logs.
Query raw logs using Log Explorer
You can switch to Log Explorer Beta to dive deeper on your analysis while applying the same filters you used in Security Analytics. Raw logs in Security Analytics are based on the same data source used in Log Explorer.
Final remarks
The Security Analytics dashboard uses sampled data, except when showing raw logs. Most information in the dashboard is obtained from httpRequestsAdaptiveGroups and httpRequestsAdaptive GraphQL nodes. For more information on working directly with GraphQL datasets, refer to Datasets (tables).